
Call Us : IDN +62-21-572-4712 – JPN +81-048-553-4655
Call Us : IDN +62-21-572-4712 – JPN +81-048-553-4655

Honeypot networks are sophisticated security mechanisms designed to attract and detect cyber attackers. These decoy systems look like genuine network resources, but are actually fake, creating an attractive target for hackers. By monitoring and analysing the activities within these honeypots, security professionals can gather valuable intelligence on attack methods and strategies. This information is crucial to help improve overall network security and protect the real systems from potential attacks.
This article explores the concept of honeypot networks, explains how they can be strategically deployed, and discusses their crucial role in strengthening cybersecurity.
Honeypot networks represent a proactive cybersecurity strategy, instead of just anticipating attacks. Organization deploys dummy systems or services within their networks to trick and trap malicious hackers. These decoys, which look just like real assets, draw in attackers while luring them away from the real network, allowing defenders to learn about their methods and strategies. By guiding attackers into a controlled environment, honeypot networks enable defenders to detect, study and respond to threats more effectively.
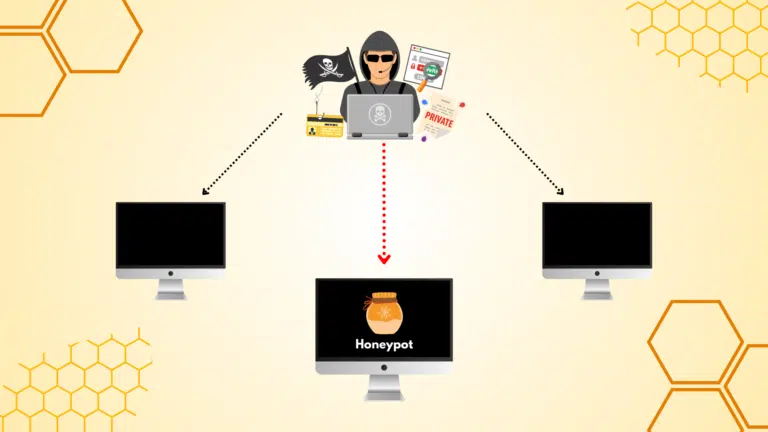
Deception and Deterrence: Honeypot networks serve as digital traps, diverting attackers away from critical assets and into a simulated environment. By presenting tempting targets full of vulnerabilities, defenders disrupt adversary operations and lower the risk of real-world breaches.
Intelligence Gathering: Analysing the insights gained from each interaction with a honeypot, including scouting, hacking attempts, and lateral movement, helps defenders better understand emerging threats. This understanding enables them to proactively strengthen defences and prevent risks.
Early Threat Detection: Honeypot networks also function as early warning systems, detecting and notifying defenders of suspicious activities that traditional security measures might miss. Identifying threats early enables organizations to respond quickly, stopping potential breaches before they become serious.
Low-Interaction Honeypots: These simulate basic services or protocols with minimal interaction, making them suitable for broad-scale deployment across the network. While they provide limited insight into adversary behavior, they are valuable for their ease of deployment.
High-Interaction Honeypots: In contrast to low-interaction honeypots, these create a completely immersive experience for attackers, emulating authentic systems and applications. Despite being resource-intensive, they provide detailed insights into adversary tactics for comprehensive threat analysis and response.
Decoy Networks: Strategically positioned throughout the network topology, these networks consist of interconnected honeypots. Decoy networks consist of interconnected honeypots strategically dispersed throughout the network topology. By mirroring the organization’s infrastructure, decoy networks expand the deception footprint and enhance threat visibility across various attack vectors.

Strategic Placement : To mimic high-value assets while avoiding detection, honeypots should be strategically positioned. Employing network segmentation and traffic redirection mechanisms can enhance their effectiveness.
Resource Allocation : To sustain honeypot deployments, sufficient resources—including hardware, software, and personnel—must be allocated. Continuous monitoring and refinement are essential to maintain the integrity and effectiveness of the decoy environment.
Integration with Cyber Defence Frameworks : To enhance situational awareness and facilitate proactive threat mitigation, honeypot networks should seamlessly integrate with existing cybersecurity frameworks, such as SIEM (Security Information and Event Management) systems and threat intelligence platforms.
In the ongoing battle against cyber threats, organizations need to adopt innovative tactics to protect their networks and preserve vital assets. Honeypot networks provide a proactive approach to detecting, diverting, and deterring attacks, all while gathering intelligence to promote cyber resilience. Contact your IT partner today and consult on the strategic deployment and effective management of honeypot networks to safeguard your organization’s security.
Reference Link :
Spitzner, L. (2003). “Honeypots: Tracking Hackers.” Addison-Wesley Professional.
Provos, N., & Holz, T. (2008). “Virtual Honeypots: From Botnet Tracking to Intrusion Detection.” Addison-Wesley Professional.
Mchugh, J., & Christie, A. (2009). “Network Security with OpenSSL: Cryptography for Secure Communications.” O’Reilly Media.
Northcutt, S., & Zeltser, L. (2003). “Inside Network Perimeter Security: The Definitive Guide to Firewalls, VPNs, Routers, and Intrusion Detection Systems.” Sams Publishing.
Spitzner, L. (2002). “Know Your Enemy: Learning About Security Threats.” Addison-Wesley Professional.
Author :
Editor : Anggita Rukmawardani